Microsoft Exchange servers worldwide hit by stealthy new backdoor
[ad_1]

Getty Images
Researchers have identified stealthy new malware that threat actors have been using for the past 15 months to backdoor Microsoft Exchange servers after they have been hacked.
Dubbed SessionManager, the malicious software poses as a legitimate module for Internet Information Services (IIS), the web server installed by default on Exchange servers. Organizations often deploy IIS modules to streamline specific processes on their web infrastructure. Researchers from security firm Kaspersky have identified 34 servers belonging to 24 organizations that have been infected with SessionManager since March 2021. As of earlier this month, Kaspersky said, 20 organizations remained infected.
Stealth, persistence, power
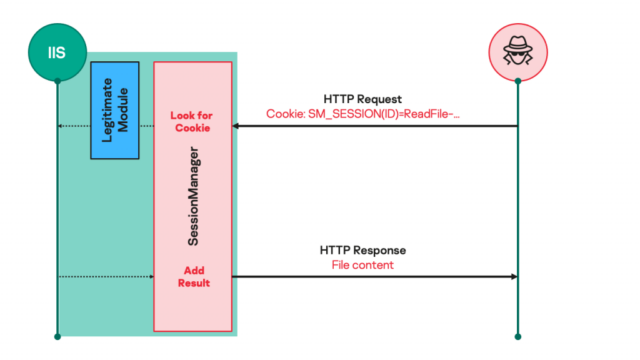
Malicious IIS modules offer an ideal means to deploy powerful, persistent, and stealthy backdoors. Once installed, they will respond to specifically crafted HTTP requests sent by the operator instructing the server to collect emails, add further malicious access, or use the compromised servers for clandestine purposes. To the untrained eye, the HTTP requests look unremarkable, even though they give the operator complete control over the machine.
“Such malicious modules usually expect seemingly legitimate but specifically crafted HTTP requests from their operators, trigger actions based on the operators’ hidden instructions if any, then transparently pass the request to the server for it to be processed just like any other request,” Kaspersky researcher Pierre Delcher wrote. “As a result, such modules are not easily spotted by usual monitoring practices: they do not necessarily initiate suspicious communications to external servers, receive commands through HTTP requests to a server that is specifically exposed to such processes, and their files are often placed in overlooked locations that contain a lot of other legitimate files.”
Kaspersky
Once SessionManager is deployed, operators use it to profile the infected environment further, gather passwords stored in memory, and install additional tools, including a PowerSploit-based reflective loader, Mimikat SSP, ProcDump, and a legitimate Avast memory dump tool. Kaspersky obtained multiple SessionManager variants that date back to at least March 2021. The samples show a steady evolution that has added more features with each new version. The most recent version of the malicious module includes the following:
Command name
(SM_SESSION cookie value)Command parameters
(additional cookies)Associated capability GETFILE FILEPATH: path of file to be read. FILEPOS1: offset at which to start reading, from file start. FILEPOS2: maximum number of bytes to read.
Read the content of a file on the compromised server and send it to the operator as an HTTP binary file named cool.rar. PUTFILE FILEPATH: path of file to be written. FILEPOS1: offset at which to start writing.
FILEPOS2: offset reference.
FILEMODE: requested file access type.
Write arbitrary content to a file on the compromised server. The data to be written in the specified file is passed within the HTTP request body. DELETEFILE FILEPATH: path of file to be deleted. Delete a file on the compromised server. FILESIZE FILEPATH: path of file to be measured. Get the size (in bytes) of the specified file. CMD None. Run an arbitrary process on the compromised server. The process to run and its arguments are specified in the HTTP request body using the format: <executable path>\t<arguments>. The standard output and error data from process execution are sent back as plain text to the operator in the HTTP response body. PING None. Check for SessionManager deployment. The “Wokring OK” (sic.) message will be sent to the operator in the HTTP response body. S5CONNECT S5HOST: hostname to connect to (exclusive with S5IP). S5PORT: offset at which to start writing.
S5IP: IP address to connect to if no hostname is given (exclusive with S5HOST).
S5TIMEOUT: maximum delay in seconds to allow for connection.
Connect from compromised host to a specified network endpoint, using a created TCP socket. The integer identifier of the created and connected socket will be returned as the value of the S5ID cookie variable in the HTTP response, and the status of the connection will be reported in the HTTP response body. S5WRITE S5ID: identifier of the socket to write to, as returned by S5CONNECT. Write data to the specified connected socket. The data to be written in the specified socket is passed within the HTTP request body. S5READ S5ID: identifier of the socket to read from, as returned by S5CONNECT. Read data from the specified connected socket. The read data is sent back within the HTTP response body. S5CLOSE S5ID: identifier of the socket to close, as returned by S5CONNECT. Terminate an existing socket connection. The status of the operation is returned as a message within the HTTP response body.
Remember ProxyLogon?
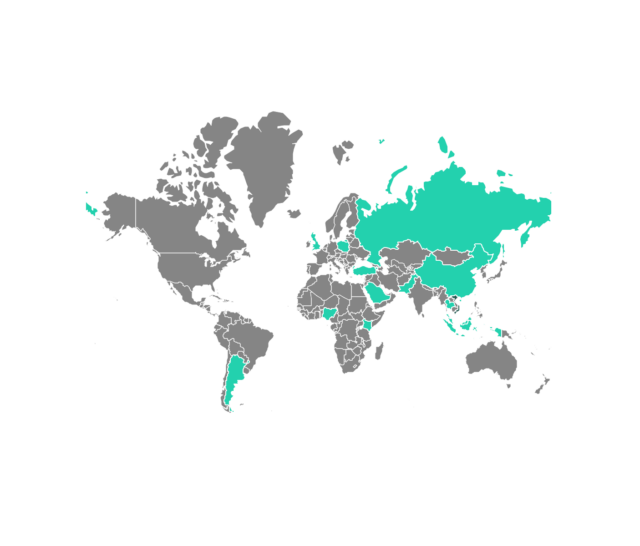
SessionManager gets installed after threat actors have exploited vulnerabilities known as ProxyLogon within Microsoft Exchange servers. Kaspersky has found it infecting NGOs, governments, militaries, and industrial organizations in Africa, South America, Asia, and Europe.
Kaspersky
Kaspersky said it has medium-to-high confidence that a previously identified threat actor that researchers call Gelsemium has been deploying SessionManager. Security firm ESET published a deep dive on the group (PDF) last year. Kaspersky’s attribution is based on the overlap of code used by the two groups and victims targeted.
Disinfecting servers that have been hit by SessionManager or similar malicious IIS modules is a complicated process. Kaspersky’s post contains indicators that organizations can use to determine if they’ve been infected and steps they should take in the event they’ve been infected.
Source link